NetScaler Gateway - 2FA Token Rewriting
With the introduction of the Portal Themes option by Citrix, administrators now have a simple, upgradeable and reasonably large amount of options when it comes to customising the look and feel of the NetScaler Gateway page and recently AAA sign in pages. There are still however some modifications which can’t be done through the Portal Themes page and have to be implemented via code changes.
Traditionally this has meant one of two paths:
- Modifications via netscaler.rc or the Custom Theme method
- NetScaler Rewrites to change pages on the fly
Due to the fact that Portal Themes supports a large number of changes I see clients are now staying away from using custom themes wherever possible. Instead of using custom themes, we can make a large number of CSS changes within the Portal Theme CSS files (more on this in a future post) and the rest can be handled with a Rewrite or two.
In this post I will detail a Rewrite method you can use to switch the second Password 2 input box from a password field to a text field. The end result is that users won’t have their two factor authentication code hidden when inputting it. This article also serves as a good example for making changes to any other elements of the NetScaler Gateway page.
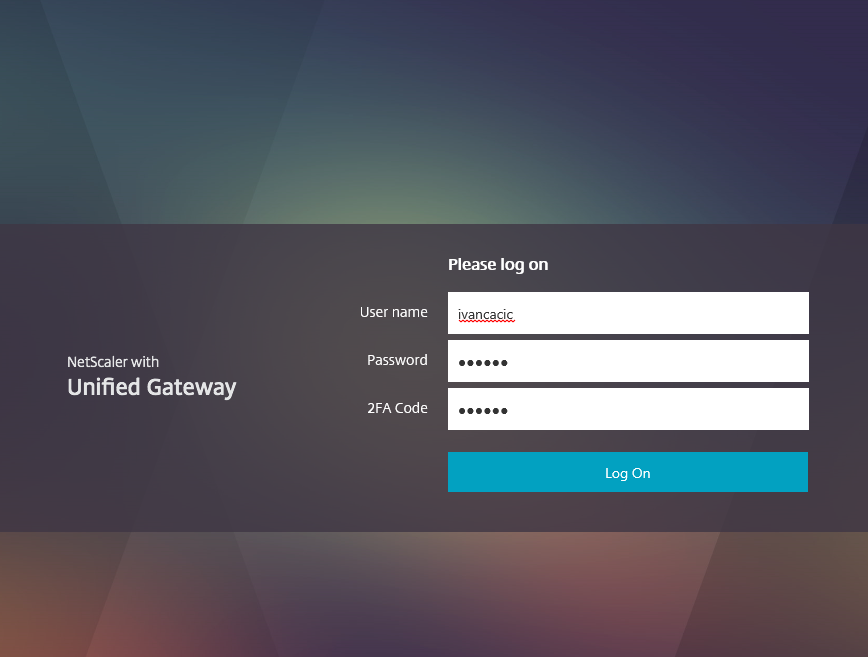
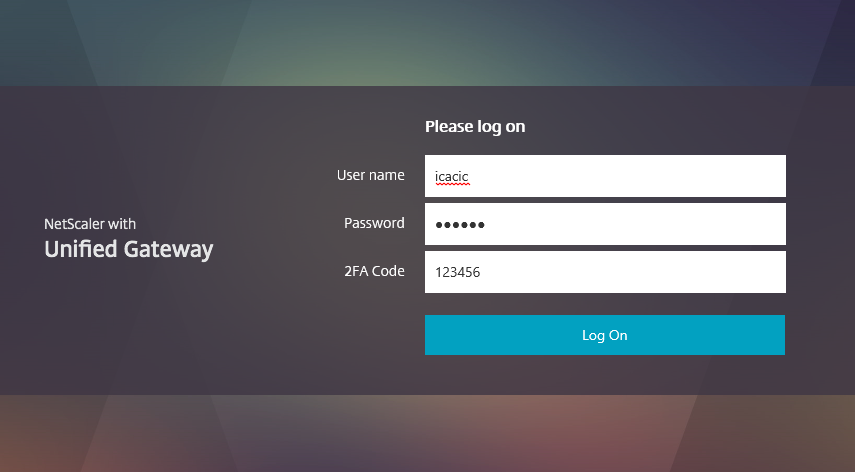
Let’s begin by having a look at the default X1 theme with 2 authentication methods defined, I have changed the Password 2 field to say 2FA Code in my example:
We can see the second password box is obfuscating the code I have entered. The form is generated by the gateway_login_form_view.js`` page located under thevpn/js/``` URL path, if we open the page up we can find the relevant line (#39) here:
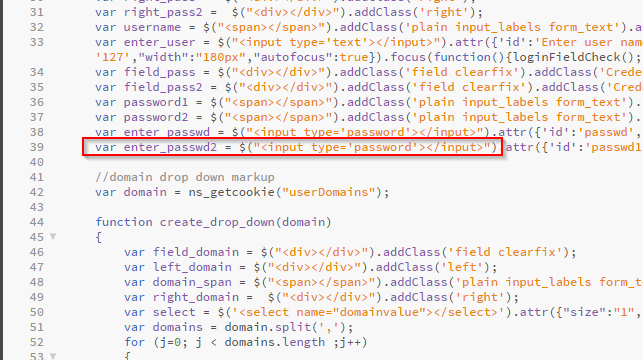
What we want to do is switch the var enter_passwd2 = $("<input type='password'></input>") section to var enter_passwd2 = $("<input type='text'></input>")
The above switch means that the input box is generated with a text type rather than an obfuscated password type, this is the same input box type as the username field box.
If you’re targeting something other than the contents of the gateway_login_form_view.js page you will need to do some digging to work out where and how the element is being created, for this I recommend Chrome Developer Tools (F12).
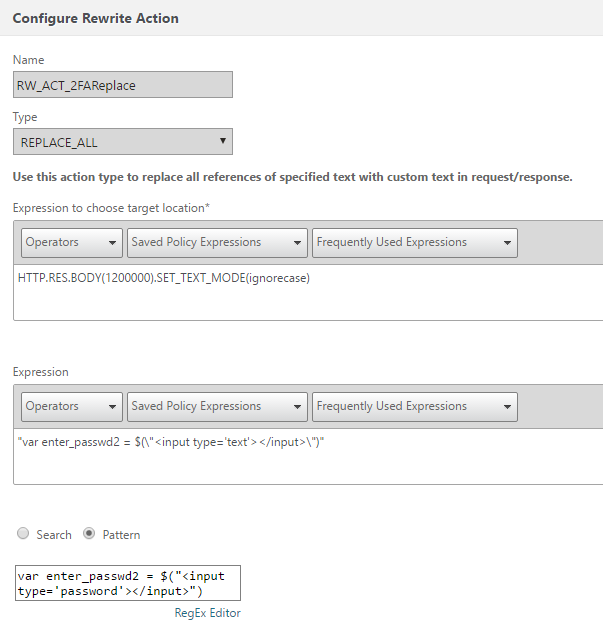
The Rewrite policy and action we create are both quite straight forward, let’s have a look at the action first (you can access the Rewrite section under NetScaler > AppExpert > Rewrite):
The action is of type REPLACE_ALL, this will change ALL matching patterns, we could probably get away with just the REPLACE type. The expression targets the first 1200000 character of the response body and drops case sensitivity (we could (and probably should) lower the character number size to reduce CPU usage).
The Pattern includes the variable which we are trying to find and the Expression is the change we are making to the Pattern.
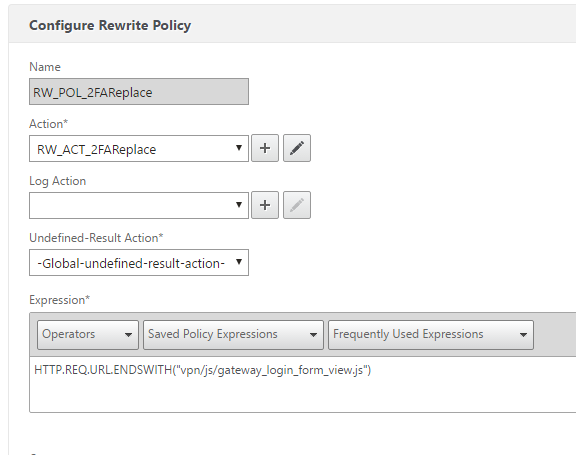
To limit the burden on the NetScaler Rewrite function our policy is targeted down to the vpn/js/gateway_login_form_view.js URL, it looks like this:
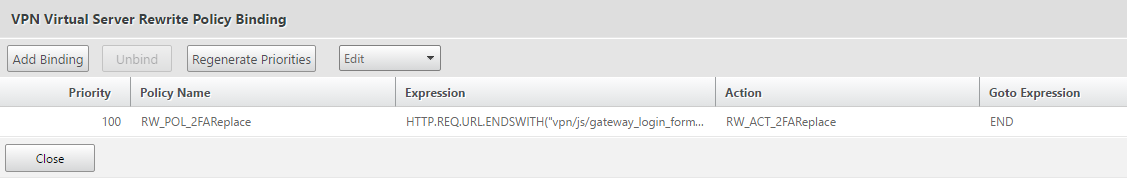
The final step is to bind the rewrite policy to your NetScaler Gateway, the NG should already have some Session Policies bound, under the Policies section of the NG you wish to target, click the + button and select the Rewrite option, the Rewrite will be activated when responding to users accessing the gateway_login_form_view.js page and thus we should select the Response option.
Select your policy and bind it to the NG:
Now let’s check on our NG:
Give me the commands
For those comfortable with the CLI you can use the following commands to perform the same actions without going through the GUI:
add rewrite action RW_ACT_2FAReplace replace_all "HTTP.RES.BODY(1200000).SET_TEXT_MODE(ignorecase)" q{"var enter_passwd2 = $(\"<input type='text'></input>\")"} -pattern "var enter_passwd2 = $(\"<input type=\'password\'></input>\")"
add rewrite policy RW_POL_2FAReplace "HTTP.REQ.URL.ENDSWITH(\"vpn/js/gateway_login_form_view.js\")" RW_ACT_2FAReplace
bind vpn vserver citrix.ivancacic.com -policy RW_POL_2FAReplace -priority 100 -gotoPriorityExpression END -type RESPONSE
Troubleshooting
There are a number of issues which can occur when attempting the above, some common ones to be wary of:
- Make sure you are licensed for Rewrite on the NetScaler appliance (Enterprise or above)
- Make sure you are targeting the correct file and using the correct string - future and past firmware version will more than likely have different strings
- If your changes don’t come through, Integrated Caching may be to blame, even if you are not licensed for it, you can clear it by following this part of my last post